When it comes to cybersecurity,
you are our call to action.
Protect and prepare against cyber threats with custom network protection services and anti-phishing efforts

Full-scale cybersecurity stack, managed by our experts
Limited budgets, a lack of skilled staff, and talent shortages make it challenging to identify the right people and technology to launch a cybersecurity program in-house. Still, protection against phishing, spoofing, and ransomware attacks is vital. Our local, experienced, and vigilant agents are on call and accessible 24/7/365.
To be effective against cybersecurity threats, your business needs to:
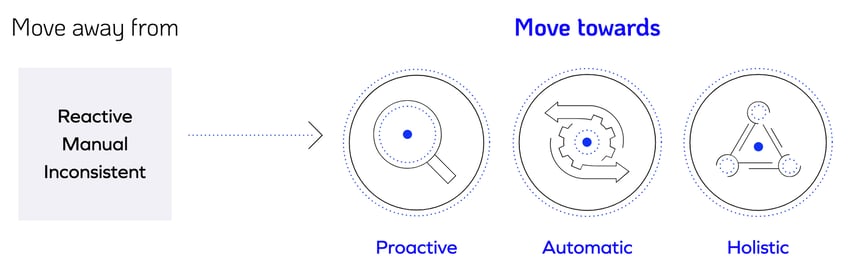
Why DOT?
As your managed security service provider (MSSP), we provide proactive monitoring and an individual approach so you get the most out of each program, along with expert handling when a bad actor tries to find the cracks in your system.
Take our phishing quiz today to test your knowledge, learn more about phishing statistics, and discover cybersecurity best practices.

Solutions
Endpoint Protection is a set of cybersecurity tools that protect each individual device on your network. DOT Security's endpoint protection services fortify devices as entry points to your network.
Backup and disaster recovery is a suite of solutions that allows your environment to be restored in the case of a total system failure. Whether it’s due to a cyberattack or natural disaster, by backing up your data in a secure location and creating a plan for disaster recovery, you ensure that your network can rebound quickly when faced with a data breach.
Edge security is threat prevention, detection, and mitigation for your entire network, no matter how your employees connect to it, with firewalls, antivirus software, and internal systems protection. It integrates Unified Threat Management (UTM) and a Web Application Firewall (WAF) to protect sensitive apps and data and control internet traffic.
Network security monitoring is regular, cyclical surveillance of a system to find any cyberattacks or breaches that may have slipped through the cracks unnoticed.
Compliance services are the way you ensure your company’s cybersecurity is in line with industry- and location-based standards and regulations, as well as modern consumer expectations when it comes to data privacy.
Cybersecurity consulting is the series of ongoing conversations with experts about the best way to protect your company’s network and data against cyberattacks. It's also training for your employees to ensure they're aware of modern security best practices.
Identity and access management is a set of tools and training that can be implemented in your company to keep your login credentials secure and prevent attackers from accessing and moving around in your system.
Secure data protection refers to a set of measures designed to fortify your most critical business information. Whether it’s details about your company or your clients, virtually every organization handles sensitive files. Our data protection services secure this information through a multilayered stack of solutions.

What you get when you work with DOT Security
Our process breaks down into three components: people, approach, and technology. Experts control the system. Our method covers all the bases for thorough, proactive care. And our tools provide comprehensive cybersecurity. Take a look at our process below:
- Assess your environment
- Advise your security posture
- Design a holistic approach
- Deploy your solution
- Manage through its life cycle
